Domain Controller: DCNL01.domainA.com
Test user : userA pass:Pumpkin1
sso binding user: ssoA pass: Pumpkin1App
LDAP principal : [email protected] pass:Pumpkin1
DC: DCNL02.domainB.com
Test user: userB pass:Pumpkin1
sso binding user: ssoB pass:Pumpkin1App
LDAP principal :[email protected] pass:Pumpkin1
Forest DomainApp.com
DomainApp.com
DC: DCNL03.domainApp.com
WorkStation: DSKNL03
Test user: userApp pass:Pumpkin1
sso binding user: ssoApp pass:Pumpkin1App
V11CON01.domainApp.com – Weblogic server
LDAP: WLSAdminApp pass:Pumpkin1
Application (Weblogic) server installed in DomainApp.com
Application Users created in all 3 domains.
Service users for LDAP and SSO created in each domain.
Important: KRB Principal should all have the same passwords, key version numbers, and encryption types.
sso user: [email protected] pass:Pumpkin1App
sso user: [email protected] pass:Pumpkin1App
sso user: [email protected] pass: Pumpkin1App
DNS resolution need to be in place.
LDAP
Weblogic configured with 3 LDAP authentications. Order is important. If you put asserter before DomainB, domainB will do only LDAP.
SSO
SSO command run on each DC:
DCNL03.domainApp.com
Setspn: setspn -A HTTP/v11con01.domainapp.com ssoApp
Ktpass run: ktpass -out SSOKeyTabFile -kvno 0 -princ HTTP/[email protected] -mapuser ssoApp -pass Pumpkin1App -crypto RC4-HMAC-NT
Ssokeytab collected (out SSOKeyTab) and we will use it for our Weblogic.
Full output of ktpass command :
DCNL01.domaina.com
Setspn: setspn -A HTTP/v11con01.domainapp.com ssoa
Ktpass run: ktpass -kvno 0 -princ HTTP/[email protected] -mapuser domainssoa -pass Pumpkin1App -crypto RC4-HMAC-NT
DCNL02.domainb.com
Setspn: setspn -A HTTP/v11con01.domainapp.com ssob
Ktpass run: ktpass -kvno 0 -princ HTTP/[email protected] -mapuser domainbssob -pass Pumpkin1App -crypto RC4-HMAC-NT
Files for SSO created on application server
Krb5.ini (Located in C:Winnt)
krb5login.conf
SSOKeyTabFile (generated on the first DC)
After deploying our application we can test sso:
Tickets from workstation in domaina.com
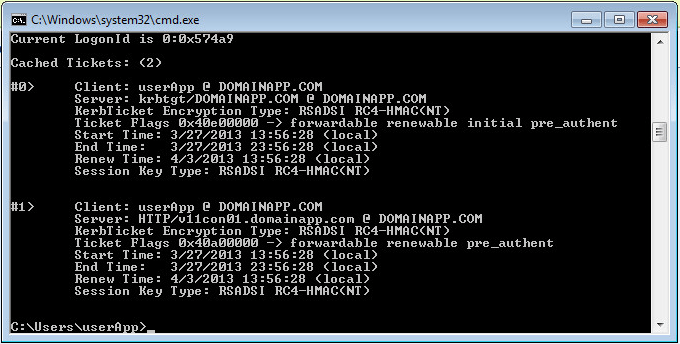
Tickets from workstation in domainApp.com
Tickets from workstation in domainB
Natalya ([email protected])







Hi Natalya,
What a great post! thank you!
I would like to ask if you can give me some guidelines on setting sso for the following env:
The weblogic domain is installed on a machine which belong to domainA.com, and the spn is set in domainA.com.
However, the weblogic domain draws its users from domainB.com.
Thank you.
In addition the two AD domains have only external trust set between them and not full trust. (when I said domain by the way, I meant DC)